In a time when attacks are as complicated as the network they are targeting, perimeter defense, monitoring your network edge through Intrusion Detection and Prevention Systems (IDPS) and End-Point Detection and Response (EDR), is important but not sufficient. In today’s network environment, you must also monitor your internal network traffic, often referred to as East-West traffic for effective threat detection and response.
Here are the areas we cover:
- The Rise of Cyberattacks
- Traditional Security Monitoring
- Insider Threats
- Capturing Network Traffic
- Axellio PacketXpress
The Rise of Cyberattacks
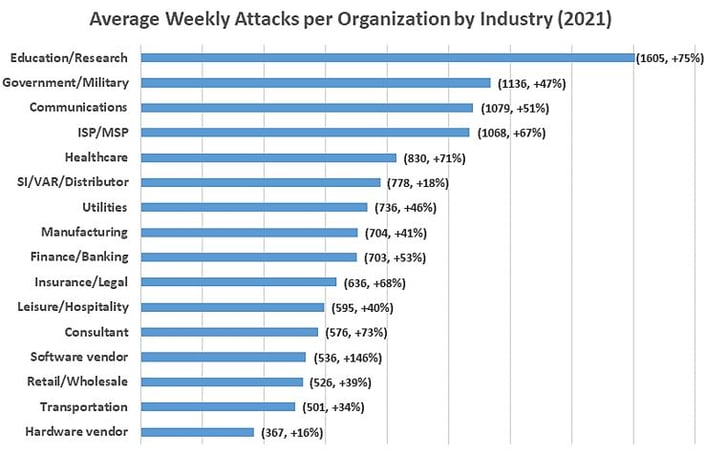
A recent study from Check Point Research suggests that the current security monitoring approach is ineffective and that many organizations are at risk, even when they have a strong perimeter defense. In North America alone, we saw an average of 503 weekly attacks per organization in 2021, which was a 61% increase over the previous year, with the highest average cost of damages in over 17 years. In this recent Check Point Research global study, Check Point documented a year-over-year increase of 50% per week in attacks on corporate networks globally, and almost as much on government and military organizations.
Check Point Research Jan 2022
Source: Check Point Research: Cyber Attacks Increased 50% Year over Year - Check Point Software
Unfortunately, hackers are now much better prepared than they were in years past. Instead of the previous common “grab-and-run” attacks, major threat actors now carefully plan and study their targets for several months, in order to inflict maximum damage. These Advanced Persistent Threats (APT) are designed to steal information over a long period of time, rather than infiltrating the network and leaving quickly after. IBM Security, in its “2021 Cost of a Data Breach Report,” shows that it can take 212 days from compromise to detection for the average attack, which slows down an organization's incident response. That means a total of seven months of exploration by the threat actors until they are discovered, significantly maximizing their impact.
Learn Why the Current Security Monitoring Approach is Ineffective
Is the Traditional Security Monitoring and Network Monitoring Approach Still Sufficient?
As discussed above, the current network security monitoring approach leaves organizations vulnerable to attacks and breaches. Even though today’s network monitoring and security tools are growing ever more sophisticated and “intelligent,” the primary defenses most organizations use are still based on concepts developed 30 years ago: firewalls, intrusion detection systems (IDS), and endpoint protection in combination with device information such as logs, events, and other digital forensics. Over the past few years, some organizations started to use network traffic monitoring at strategic points in their network utilizing network detection and response (NDR) solutions. However, even though the information obtained has been significantly enriched and refined, threat actors have had plenty of time to evolve their attack approaches to circumvent traditional defenses.
.png?width=952&name=Images%20for%20Pillar%20Page%20Blogs%20(2).png)
Infographic: Network and Security Monitoring Infrastructure is Complex and Incomplete
Perimeter defense is still the essential first line against attackers, but organizations have a difficult time defining their perimeter. This is because the physical network extends into the cloud, the home network of their employees, or even coffee shops and hotels of their road warriors. With this increased mobility and exposure, once a device is compromised, threat actors have free rein, due to the limited segmentation in most networks that would otherwise limit the threat actors’ lateral movements. Perimeter defense tactics only assess a minority of the total enterprise traffic, leaving most of the traffic unsecured and unwatched. In order to better assess the threats to our internal network, we need to monitor strategic points in the network to see the remaining traffic.
Firewalls, intrusion detection and prevention systems (IDPS), and endpoint protection products are still the most common tools to detect and keep threat actors out. However, this concept is based on the outdated assumption of trusted vs. untrusted networks: your managed network on the inside of your organization being trusted and known, the outside world being untrusted.
Zero Trust can help network detection and response issues by constantly validating any action an endpoint is taking in the network while considering even the internal network a “hostile” environment. However, Zero Trust requires significant changes across the entire application delivery chain and can take years (if not decades) to implement.
Read Our Blog on Perimeter Defense
Insider Threats - The Dangers Inside Your Network
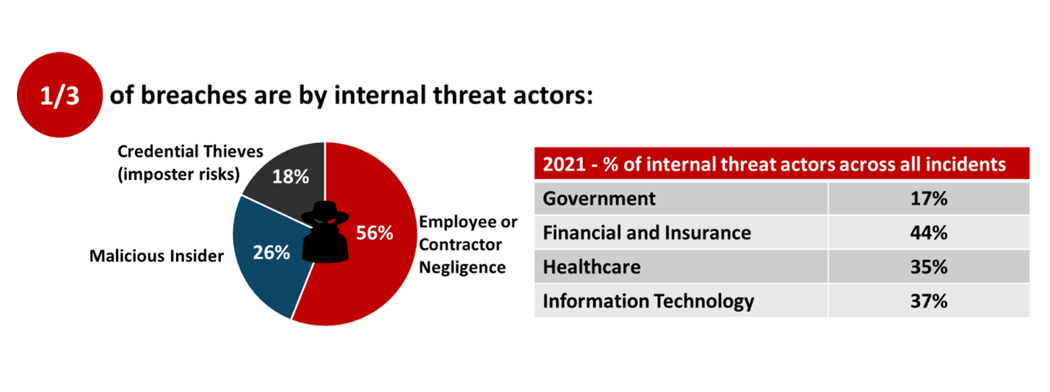
Verizon in its recent “2021 Data Breach Investigations Report” identified that almost one-third of breaches are by internal threat actors. Insider threats are any unapproved or malicious insider use of resources, intentional or unintentional. With 94% of all malware being delivered via email, employee negligence still makes up for the majority of insider threats. Email is a good delivery vehicle for attackers as it allows for a direct installation by users who already have access to critical systems. Only about 18% of breaches are because of stolen credentials. Once attackers are inside your network, they can hide for weeks or even months, exploring your environment and laying the groundwork for an attack.
2021 Data Breach Investigations Report, Verizon
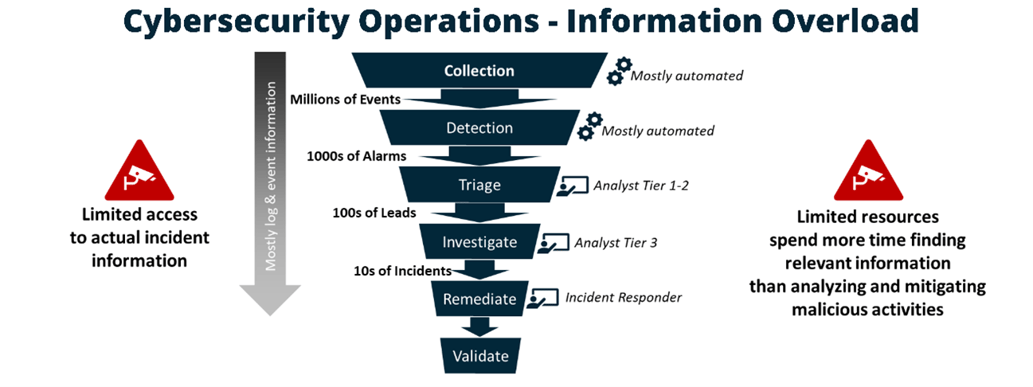
Most large enterprise organizations receive millions of events per day from their network and security infrastructure. The MITRE ATT&CK® framework identifies 38 data sources essential for tracking the many attack vectors, including process, file, command, and network traffic.
This creates millions of events per day for any large organization. In addition, these events must be cross-correlated and analyzed. Security Information and Event Management (SIEM) systems have been deployed to reduce this onslaught of events, but these events also need to be further analyzed and reduced by security analysts to identify the select few incidents that need to be investigated. Few of these incidents are ultimately resolved and remediated because none of the events really provide a complete picture of the situation.
In addition to data overload, security operations are also overwhelmed by the number of tools they utilize in their security infrastructure. Palo Alto Networks reported that medium sized businesses use on average 50-60 security tools, and large organizations use as many as 130 security tools on average.
There are too many logs, events, alarms and even tools used to reliable correlate and assess the data. But, today’s data requires to correlate multiple data sources to build a complete picture quickly assess, triage, and mitigate threats.
Download the Network and Security Monitoring Infrastructure Infographic
Capturing Network Traffic
Many organizations limit their monitoring only to high-aggregation points, especially network ingress and egress (North-South interfaces). However, these high-aggregation points only account for 15% of the total enterprise traffic which is especially dangerous with the increasing internal threats.
Just relying on metadata is no longer sufficient. Threat actors have taken advantage of this limited visibility by concealing their activities on the network from your security team. They hide their activity within perfectly legitimate traffic by properly encoding the packet header information, as most network traffic analysis applications only analyze the protocol headers. Attackers may even spoof application specific header information to fool Deep Packet Inspection tools. Therefore, monitoring both North-South (external or ingress/egress) and East-West (internal) network traffic and capturing packet data is essential to make rapid and informed decisions. Only having meta-data gives attackers opportunities to mask their activity and traverse your network without detection.
Download the Packet Loss Infographic
The Importance of Packet Data
Over the last decade, the industry has settled on making decisions on mostly meta-data as this information is readily available and can be easily stored. Despite the fact that capturing the actual traffic in the form of packets provides a much richer set of data, it has been dismissed as too complex and expensive and is only employed sparingly. This leaves many organizations with data that is overwhelming in volume but often insufficient for rapid incidents response.
Capturing actual traffic in the form of packets provides a much richer set of data for Network Operations and Security Operations teams. These packets offer immutable evidence of how an attacker entered your network, what actions they took, and the packets are nearly impossible for hackers to delete or modify. When captured, this provides a rich data set that can be analyzed pre-and post-event to determine how attackers entered the environment, what actions they took, and which devices were communicated with.
Capturing and recording network packets is essential for forensic and root cause analysis to secure networks and ensure their operation. Despite the value and insight PCAP provides, many organizations only employ this selectively and reactively after an event has been detected – often too late to capture the actual incident. Current packet capture appliances are also limited, creating even more problems for organizations that want secure networks. Many of them are complex inflexible, expensive, and only allow for limited access to the data you need.
It is time to rethink this approach.
Read Our Blog on Streamlining Threat Detection and Incident Response Through Packet Data
Axellio PacketXpress®
Your organization’s security solution should align with your objectives, needs, and infrastructure to create a comprehensive and effective security stack and process. This allows you to prioritize what matters for rapid and informed decisions and enables your response across your entire threat lifecycle: from threat detection to incident response to threat hunting.
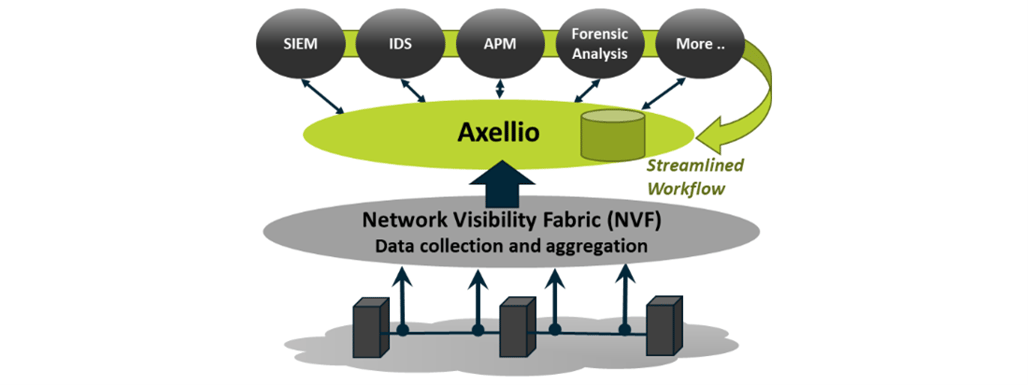
Axellio Inc. is an innovator in high-performance, 100 Gbps no-loss network traffic capture, distribution, and analysis and serves network and security operations in commercial enterprise, government, and defense. Axellio’s PacketXpress is an application-agnostic, open platform, combining common, off-the-shelve hardware with APIs to integrate with any commercial and open-source analysis solution - creating a comprehensive and economical security solution for network and security operations for better visibility.
All applications consuming packet data benefit from PacketXpress, being able to buffer traffic spikes and keep up with traffic growth. PacketXpress can smooth out traffic spikes that otherwise overload applications and lead to information loss due to its store and forward approach.
With PacketXpress inserted between the network visibility fabric and your monitoring infrastrcuture, you can more efficiently and reliably leverage the monitoring infrastructure you already have in place. This applies to all applications, whether operating on physical or virtual platforms. With the ability to pivot directly from an event into the detailed packets surrounding any event drives faster decisions on whether an event is urgent and important by directly access to complete pre-and post-event packet data with the click of a button, avoiding lengthy data collection and correlation.
PacketXpress: The Network Visibility Hub
Axellio developed PacketXpress to make your existing infrastructure more efficient in threat detection while providing the packet data needed to fully understand what happened and to engineer the right defense - quickly and efficiently.
PacketXpress applies to variety of use models and industries – learn more:
Cybersecurity
Trade Surveillance
Government and Defense
Learn more about Axellio and Our Partners
Sign up for our Axellio Insights Newsletter
Read the Cyber Threat Insights Blog
Meet our cyber threat and incident response team
See our most recent Press Releases
Learn more about Axellio’s events
Check out our Cyberthreat partner program
Ready to Improve Your Approach to Threat Detection and Response?
Axellio’s goal is to leverage the resources and tools you already have in place while providing faster access to richer, more contextual data. Prioritize what matters, for rapid and informed decisions, and for efficient response across your entire threat lifecycle: from threat detection over alert triage and incident response to threat hunting.